Filestack Features
Get the most out of your application by utilizing Filestack’s many services. Make your applications smart, add security, and create logic and workflows all within Filestack.


WAY MORE THAN A FILE UPLOADER WIDGET: A COMPLETE UPLOAD SERVICE
UPLOADS
Elegant User Interfaces
Get started quickly with minimum configuration and improve the user experience of your application using one of the three File Picker implementations.
Different Upload Methods
Beyond the picker widgets, Filestack offers easy ways to get files uploaded and ready for delivery.
Efficient
Multipart Uploads lets you upload a large file in smaller, more manageable chunks. Individual pieces are then stitched together after all parts have been uploaded. The individual part uploads can even be done in parallel.
Reliable Service Everywhere
Whether your users are on a high speed network or on a rural high latency network anywhere on the globe, Filestack’s Content Ingest Network enables transfer of files to the cloud.
Worry-Free
Ensure a 99.999% upload success rate using the Filestack Intelligent Ingestion.
Cloud Upload-Ready
Upload files from your users’ cloud provider accounts.
Organized
Automate tagging uploaded files effortlessly. Use tags to group and classify your files.
Drag and Drop
With Filestack’s Drag-and-Drop you can easily add drag and drop file uploading support to your website.
Customizable Integration
With Custom Source functionality you can add your own integration to the File Picker based either on a static list of files or dynamic integration of your choice.
Easy Cloud Storage Integration
By default, Filestack stores uploaded files to an internally managed S3 bucket. If you already have a cloud storage solution in place and would like to integrate it with Filestack, we allow that as well.
Accelerated performance your users will notice with each and every upload.
DELIVERY
Optimized Content Delivery
To empower our users with CDN delivery, Filestack partners with Fastly CDN, one of the fastest and most secure content delivery networks. Every file that is uploaded through Filestack’s File Picker or RESTful API generates a CDN URL that delivers content at a blazing speed.
Save Time with Caching
FileStack URLs are cached to ensure fast file delivery. The cached copy of any unique Filestack URL will live for 30 days – it will then be re-cached only when it is requested again.
Images for All Screens
Whether users have their images on their desktops, laptops, tablets or any other mobile devices – Filestack seamlessly integrates to provide a consistent crisp experience for the user.
File URL Customization
Personalize your file URL using the Custom CNAME feature. For example, when a user is looking to access a file, instead of seeing “cdn.filestack.com” they can see “cdn.fs.yourbusiness.com”.
Flexibility
Storage aliases are a premium feature that allows you to use Filestack transformations and other add-ons with files not uploaded through Filestack.
User-friendly Document Previews
Empower your users with an easy way to preview documents in the browser.
SECURITY
Keep Your Application Safe
Filestack is equipped with security policies to safeguard your applications.
The policy determines which actions are authorized, and the signature authenticates the policy.
Block Unauthorized Requests
Domain whitelists prevent File Picker from being embedded on unapproved websites.
Whitelisting works by blocking requests that don’t contain an approved domain in the “Origin” header.
Empower your business with an accurate, fast, and reliable document upload solution.
INTELLIGENCE
Tag Images
Detect general features of uploaded images both synchronously and through the Workflows. Filestack has partnered with best in class platforms to provide quick analysis of images and return actionable insights.
Understand Images
Detect interesting areas of an image and assess its overall saliency. Get information, visual properties, and heatmap data of your image.
Keep Images Safe for Work
Detect whether the uploaded file contains any unsafe content or it is safe for your business.
Emotions Behind Images
Detect general emotions in the uploaded images. Happiness, sadness, confusion, angry and other emotions in your photo will be detected.
Protection Against Phishing
Detect and block any malicious HTML file before it hits your storage location.
Emotions Behind Text
Filestack will let you know if your text sounds positive, negative, neutral, or mixed. Filestack can automatically detect the text language from the twelve languages it supports.
Convey Images to Words
As an intelligence service of Filestack platform, Image Captioning is able to describe your images and return captions synchronously or even through the Workflows.
Tag Videos
Uncover insights within your videos with Filestack Intelligence using state of the art machine learning to automatically organize videos, streamline processes, and make decisions about video data without the need for manual analysis.
Keep Videos Safe for Work
Video SFW helps in providing safe video content for your audience. You will be able to block videos that violates the workplace rules such as pornographic, violent or gory content.
Check Images for Copyright
Now detect images that are copyright protected. Upload a single image or millions of images, a single API call will display the copyright status of any image. This is especially useful for businesses that rely on user generated content and require their uploads to be free of copyrights.
Optical Character Recognition
OCR extracts text from images so you don’t have to. Whether you are transcribing old documents, or grabbing license plate numbers from security footage, Filestack OCR reliably extracts printed and handwritten data from your images.
Correct Document Properties
Detect your document in the image, transform it to fully fit the image, and pre-process it to reduce noise and distortion. As a result, the accuracy of the OCR engine in text extraction will be increased.
Detect Potential Threats
Scan every file upon upload for viruses and malicious programs no matter what their file type. Filestack’s virus detection capabilities support scanning every file from images and video files to PDF documents for a secure document upload every time.
Uncover insights within your images and videos with Filestack Intelligence.
TRANSFORMATIONS
Enterprise-Grade
Filestack’s Processing Engine is a very powerful system that allows developers to transform various types of files, including images, documents, and videos.
Elegant
With the Transformations UI, you can allow your users to transform their images with a beautiful, modern interface.
Your customers will be able to apply filters, adjust image sizes, and perform many other image transformations, providing them with a seamless in-app experience.
Video and Audio Processing
VIDEO TRANSCODING PROCESS
Our video and audio transcoding features help with converting the files to the type and format you would like to use in your application.
RE-RUN VIDEO TRANSCODING
Re-run the failed conversion.
GET VIDEO/AUDIO FILE METADATA
Get the metadata information of the video/audio files.
Edit Video Properties
We have several parameters that allow you to add modifications to the output video dimensions and ratios.
Video effects
Filestack offers an easy way to improve your videos by adding video effects.
Control video quality
Increasing the quality of the video is possible with Filestack’s video transcoding tasks.
See how easy it can be to instantly transform any file or image.
Images Processing
Edit Image Properties
Image Enhancements
Image Borders and Effects
Image Filters
Facial Detection
Image Conversions
Revolutionize the way you process files.
Keep users happy by giving them an organized, smart, and future-ready file upload solution.
WORKFLOWS
Workflows allow you to wire up conditional logic and image processing to enforce business processes, automate ingest, and save valuable development time.
LOW-CODE PLATFORM
We’ve coded in all the logic so you don’t have to. Immediate access to all the features you need.
ELEGANT SIMPLICITY
Easy to use logic building blocks to get to solutions out the door more quickly.
CHANGES APPLIED AUTOMATICALLY
Make modifications and see updates on-the-fly. Changes made in the UI are live the minute you hit save.
Developers love it
Filestack connects you with a multitude of services with one simple integration. You never have to worry about updating API integrations again.
Powerful API
Filestack comes with different powerful APIs for file, processing, video & audio processing, and workflows API.
Rich Documentation
With a detailed description, explanations of concepts, examples, and API documentation, you’ll be able to write your Filestack application effortlessly and quickly.
Tutorials
Read step by step tutorials and learn about Filestack’s best practices.
Dev-to-dev support
Your files are always our #1 concern. We are always here to help you get up and running and assure the best performance.
webhooks
A key part to Filestack’s file management story is our ability to provide customers with a durable, scalable, and highly configurable automated solution. Employing tools like webhooks to extend our platform allows businesses to achieve the automated efficiency they want in their platforms.
We Speak Your Language
If you’re looking to build on top of our world class API uploading infrastructure, choose from our SDKs to get started.
import * as filestack from 'filestack-js';
const client = filestack.init('YOUR API KEY');
client.upload(fileObject).then(data =>console.log(data.url));gem 'filestack'
client = FilestackClient.new('YOUR_API_KEY', security: security_object)
filelink = client.upload(filepath: '/path/to/file')$ composer require --prefer-dist filestack/filestack-php
use Filestack\FilestackClient;
$client = new FilestackClient('YOUR_API_KEY');
$filelink = $client-upload('/path/to/file');$ pip install filestack-python
from filestack import Client client = Client("")
params = {'mimetype': 'image/png'}
new_filelink = client.upload(filepath="path/to/file", params=params)
print(new_filelink.url)Javascript
Python
React
Ruby
PHP
Android
Angular
Adaptive
Swift
Ruby on Rails
GO
Java
Modernize your file upload solution to cater to your users’ every need.
A Look at Filestack’s Features
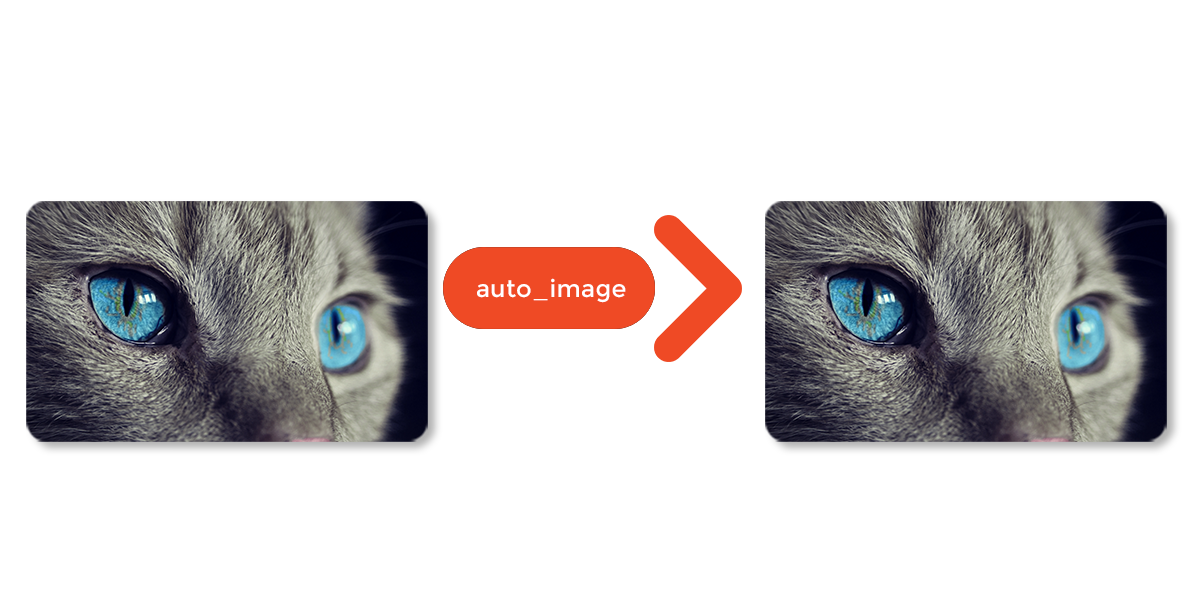
IMAGE FORMAT CONVERTER
Easily convert JPEG and PNG images to the next generation format WebP or JPEG XR which both have better compression and quality characteristics.

COPYRIGHT DETECTOR
Detect whether or not an image is copyright protected.

DOCUMENT DETECTION
Easily detect and fix rotated or folded scanned documents.
DOCUMENT VIEWER
Preview documents and files beautifully within your application and website using Filestack’s advanced Processing Engine.

FILE CONVERSION
Instantly translate images and documents created in any application to your desired format without requiring human intervention of any kind.
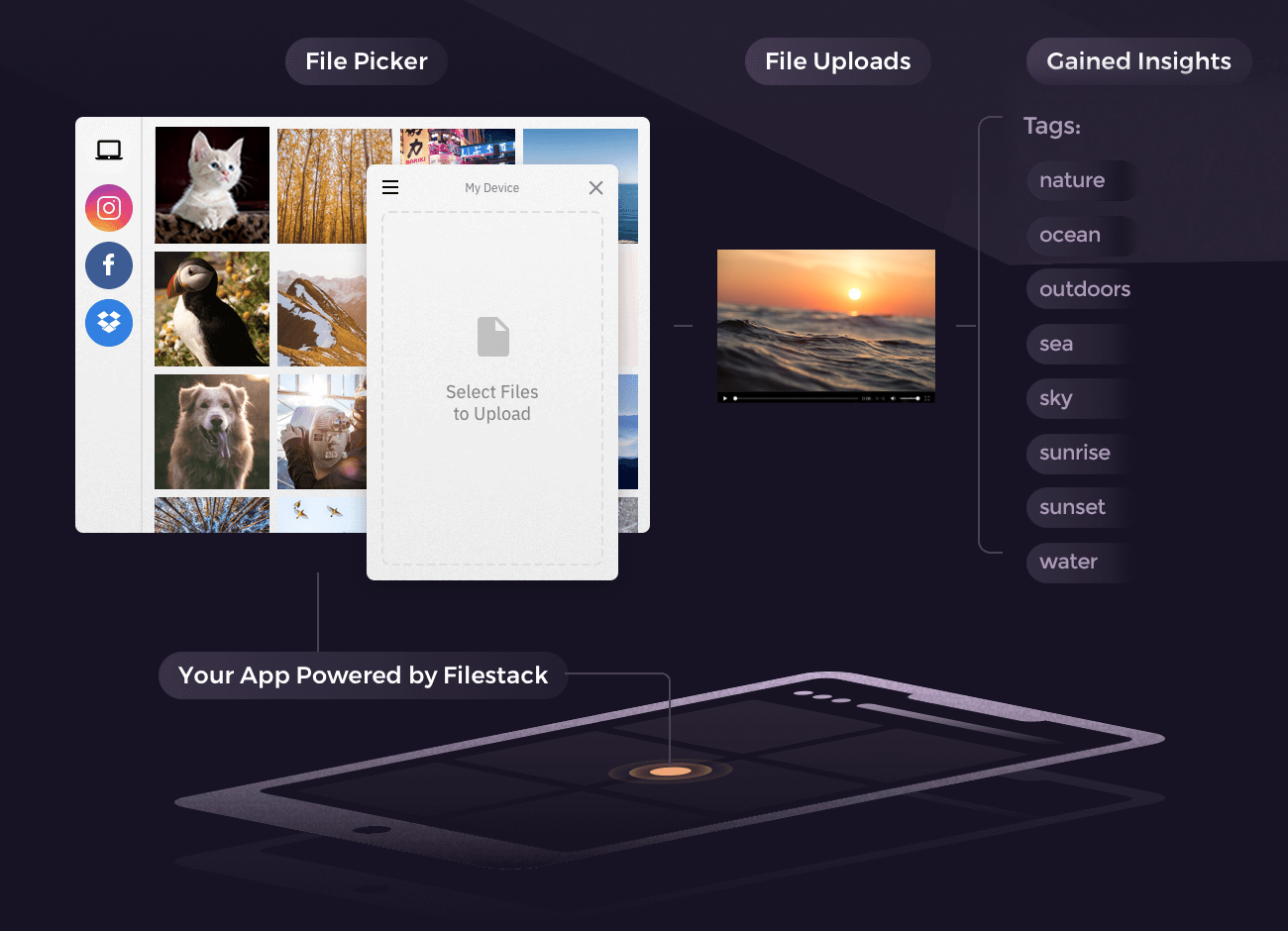
VIDEO TAGGING
Get detailed and accurate data about your uploaded videos.
DOMAIN WHITELISTS
Increase your File Picker security with domain whitelists.
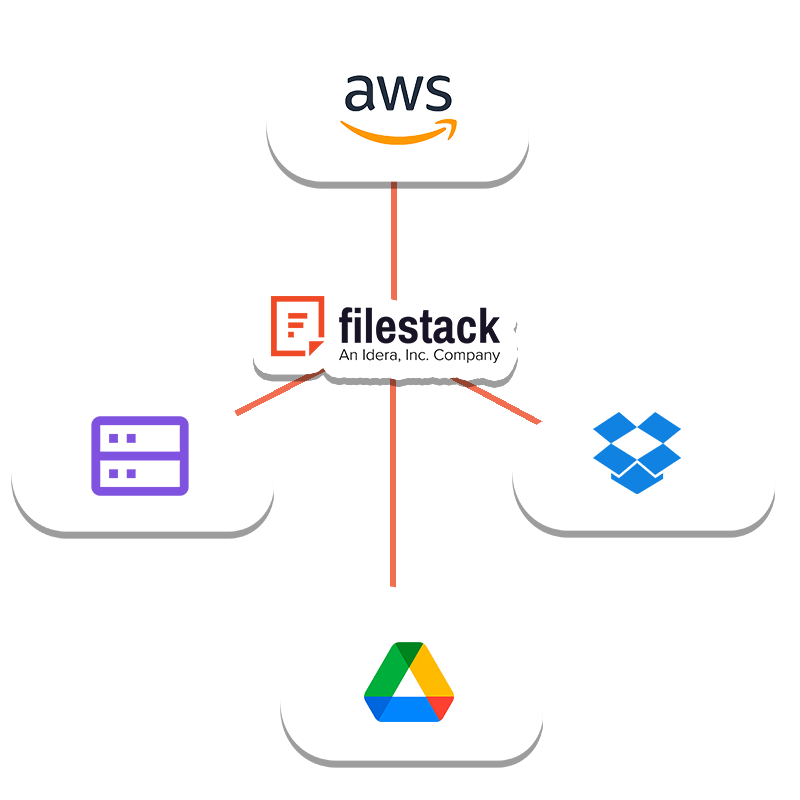
CLOUD STORAGE PROVIDER
Store your files into one of our supported storage providers and utilize the full power of Filestack’s APIs and add-ons.

DRAG AND DROP
Implement Drag and Drop Uploading feature to your application with just 3 lines of code.
 Delivery
Delivery Security
Security Intelligence
Intelligence Transformations
Transformations Video and Audio
Video and Audio Images
Images PDF
PDF File
File Workflows
Workflows Developers
Developers Recommended
Recommended